GitLab triggers to block merge requests with vulnerabilities
You can create GitLab event triggers to support a variety of STO workflows and use cases. This topic describes how to do the following:
- Trigger an STO pipeline in response to a GitLab MR that targets a protected branch and/or updates specific files.
- Include a keyword in a review comment to trigger a new scan if a previous pipeline execution failed.
The following steps outline the basic workflow:
-
Create a trigger for your Harness pipeline.
This should automatically register an outbound webhook in your Git repo.
-
Set up the failure criteria for your STO pipeline.
-
Create a merge request to test the webhook and trigger.
When you create a merge request, GitLab sends a request to the Harness webhook. If the STO pipeline fails, it sends back a
failedresponse that blocks the merge request.
Before you begin
These workflows require the following:
- A Harness connector to your GitLab account.
- A Harness pipeline with a code-repository scan step such as Semgrep.
- The Codebase in your pipeline should point to the Git repo that you want to scan.
Create the Harness trigger
The following sections describe two triggers that can be very useful in the context of STO scanning:
Trigger on a changed file
You can specify a trigger that says: If a merge request updates any of these files, run the pipeline and scan the repo.
This type of trigger supports use cases such as:
-
If the merge request updates any file that matches the trigger filter, run a SAST scan and block the PR if the scan results meet the failure criteria.
-
If the merge request updates a specific file of interest, such as a
pom.xmlworkspace file, run an SCA scan and block the PR if the scan results meet the failure criteria.
Trigger setup
-
Go to your STO pipeline, select Triggers, and add a new trigger.
-
Set up the trigger as follows.
Configuration
-
Connector to your GitLab account
-
Repository name
-
Event = merge request
-
Actions to trigger the pipeline
Condition
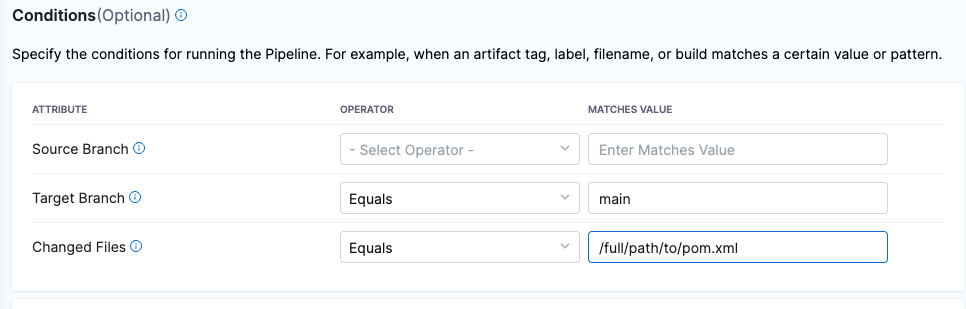
The following conditions are the most relevant to this workflow. You can add other conditions as needed. Triggers are complex filters in which all conditions are AND-ed together.
-
Target Branch This should match your target baseline, such as
main. -
Changed Files The files that trigger the STO pipeline if they have updates in the PR. You can specify multiple files using the operators In, Not In, and Regex.
Here's a simple example: trigger a build if a PR seeks to update a specific pom.xml in the main branch.
Pipeline input
The pipeline input should be configured correctly, with Build Type set to Git Pull Request.
Test the trigger
After you create the trigger, proceed to Set up the failure criteria.
YAML trigger example
trigger:
name: gitlab-trigger-on-mr-changed-file
identifier: gitlabtriggeronmrchangedfile
enabled: true
description: ""
tags: {}
orgIdentifier: default
stagesToExecute: []
projectIdentifier: sto_tutorials
pipelineIdentifier: triggertestgitlab
source:
type: Webhook
spec:
type: Gitlab
spec:
type: MergeRequest
spec:
connectorRef: your_gitlab_connector_id
autoAbortPreviousExecutions: false
payloadConditions:
- key: changedFiles
operator: Equals
value: README.rst
- key: targetBranch
operator: Equals
value: main
headerConditions: []
repoName: dvpwa-gitlab-tutorial
actions:
- Open
- Update
- Reopen
inputYaml: |
pipeline:
identifier: triggertestgitlab
properties:
ci:
codebase:
build:
type: PR
spec:
number: <+trigger.prNumber>
Trigger on a merge-request comment
You can specify a trigger that says: If a reviewer includes a specific keyword in a pull-request review comment, run the pipeline and scan the repo.
This type of trigger is useful when a pipeline execution fails for reasons other than the failure criteria you specified for the pipeline. If the STO scan doesn't finish in the original execution, a reviewer can add a review comment with a keyword such as RERUN_STO_PIPELINE.
Trigger setup
-
Go to your STO pipeline, select Triggers, and add a new trigger.
-
Set up the trigger as follows.
Configuration
-
Harness Connector to your GitLab account
-
Repository name
-
Event = Merge Request
-
Actions, such as Open, Reopen, and Edit, to trigger the scan. You can also select All actions to allow reviewers to trigger a scan at any time.
Condition
The following conditions are the most relevant to this workflow. You can add other conditions as needed. Triggers are complex filters in which all conditions are AND-ed together.
-
Target Branch This should match your target baseline.
-
Enter the following JEXL condition with the keyword to trigger a new scan:
<+trigger.payload.object_attributes.description>.contains("RERUN_STO_SCAN")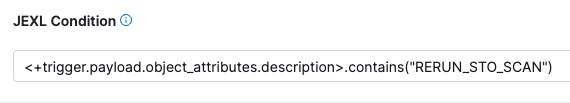
Pipeline input
The pipeline input should be configured correctly, with Build Type set to Git Pull Request.
Test the trigger
After you create the trigger, proceed to Set up the failure criteria.
YAML trigger example
trigger:
name: trigger-on-mr-comment
identifier: triggeronmrcomment
enabled: true
description: ""
tags: {}
orgIdentifier: default
stagesToExecute: []
projectIdentifier: sto_tutorials
pipelineIdentifier: triggertestgitlab
source:
type: Webhook
spec:
type: Gitlab
spec:
type: MergeRequest
spec:
connectorRef: dbothwell1gitlab
autoAbortPreviousExecutions: false
payloadConditions:
- key: targetBranch
operator: Equals
value: main
headerConditions: []
jexlCondition: "<+trigger.payload.object_attributes.description>.contains(\"RERUN_STO_SCAN\") "
repoName: dvpwa-gitlab-tutorial
actions:
- Open
- Reopen
- Update
inputYaml: |
pipeline:
identifier: triggertestgitlab
properties:
ci:
codebase:
build:
type: branch
spec:
branch: <+trigger.branch>
Set up the failure criteria
You can configure your Harness pipeline to fail if the scan finds vulnerabilities that match a specified set of criteria. You can use one of two methods:
-
Every STO scan step has a
fail_on_severitysetting that fails the step if a scan detects issues with the specified severity or higher. You can also create exemptions ("Ignore rules") for specific issues to override this behavior. -
You can use Harness Policy as Code to write and enforce policies against your security tests, and to block your pipelines if a security test has any issues that violate those policies. STO includes a set of predefined templates for blocking pipelines based on issue severity, reference ID, CVE age, title, and number of occurrences.
Test the outbound webhook and trigger
Verify the webhook in GitLab
Once you add a trigger to your pipeline, your Git service provider should create a webhook for the trigger automatically. This is true for all non-custom webhooks and all Git providers supported by Harness.
-
Go to your GitLab account and select Settings > Webhooks.
-
If you don't see a webhook, you can add one manually. For more information, go to Register the webhook in the Git provider.
Test the webhook and trigger
-
Create a merge request in your GitLab repo to verify that the trigger works as intended.
-
To verify the changed-file trigger described above:
- Go to the root branch you specified in the trigger.
- Update the file you specified in the trigger. Then create a merge request in a new branch.
-
To verify the review-comment trigger described above, create a merge request and then add a review comment with the keyword you specified.
- Go to the root branch you specified in the trigger.
- Create a merge request in a new branch.
- Add a review comment with the keyword you specified in the trigger.
-
-
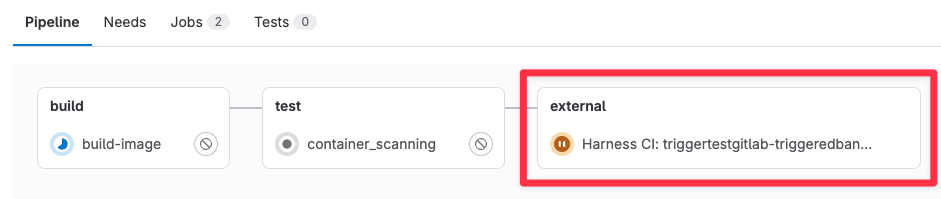
Go to the GitLab pipeline for your merge request. The STO pipeline execution appears as an external check.
When you create a merge request, GitLab creates an external status check and sends a payload to the Harness webhook. Then it waits for a response that indicates the pipeline status (
pending,passed, orfailed).For more information, go to External status checks in the GitLab documentation.
-
Go to the Pipeline Executions page of your Harness pipeline and verify that the trigger starts a new execution.
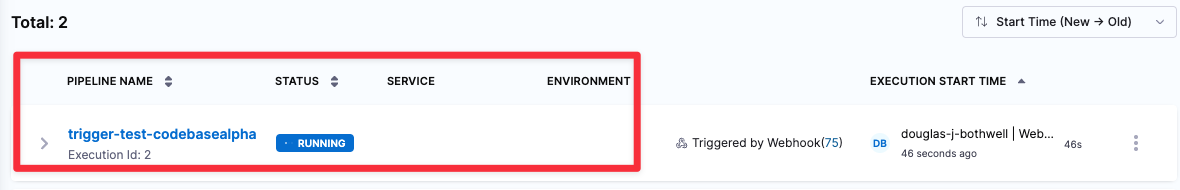
-
Go to the Merge Request page in GitLab and wait for the merge-request checks to finish.
When the Harness pipeline finishes, it sends a response to GitLab that reports the execution status. If the response is
failed, the external check fails and blocks the merge request.
If the trigger doesn't work as intended, go to Troubleshoot Git event triggers.
Test the external status check
Now that you've set up the rule, trigger another Harness pipeline execution and fail it to verify that the rule stops the merge request.
To verify the branch protection rule, you must ensure that your STO pipeline fails. To configure your pipeline to fail temporarily, you can do one of the following:
- Set Fail on Severity to Low in the scan step of your pipeline. Then scan a repo with known vulnerabilities.
- Add a temporary Run step to your pipeline with the command
exit(1).
-
Trigger another pipeline execution.
-
For the changed-file trigger described above, make and push a change. Then create a merge request.
-
For the review-comment trigger described above, add a review comment with the keyword you specified.
-
Now, merging is blocked if the Harness pipeline fails.
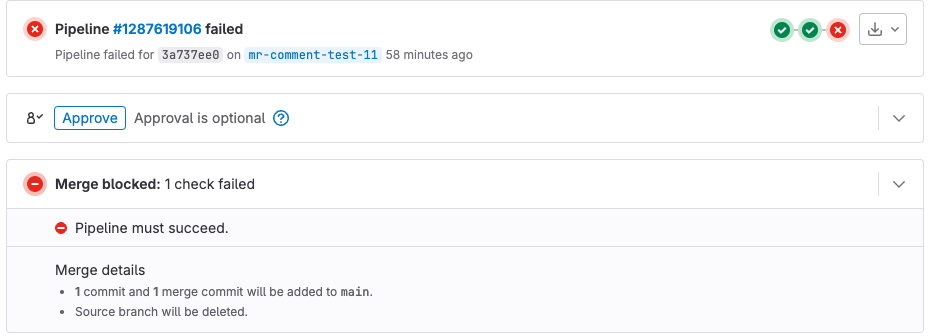
For more information
-
The Harness platform docs include extensive information about triggers. The following topics are highly relevant to STO use cases:
-
For detailed information about outbound webhooks and branch protection rules, go to the docs for your source code management (SCM) provider. This topic describes a few simple GitLab workflows, but these topics are outside the scope of Harness documentation.