Enforce SBOM policies
Enforce SBOM policies in the CI and CD stages of your Harness pipelines to ensure that your artifacts only contain approved components.
Requirements
To enforce SBOM policies in a Harness pipeline, you need:
- A pipeline with a CI (build) stage, a CD (deploy) stage, or both. You'll add the SBOM Enforcement step to one of these stages.
- SBOM OPA policies that you want to enforce.
- SBOM to compare policies against. For example, you can use SSCA to generate SBOM or import SBOM.
- A Harness file secret containing the public key from the key pair used to sign and attest the SBOM.
Add SBOM Policy Enforcement step
You can add the SBOM Policy Enforcement step to either the Build or Deploy stage of a Harness pipeline.
- In a Build stage, add the step after the SBOM generation step.
- In a Deploy stage, add the step before the deployment step.
SBOM Orchestration and Enforcement steps in deploy stage can only be used in the Containerized Step Groups
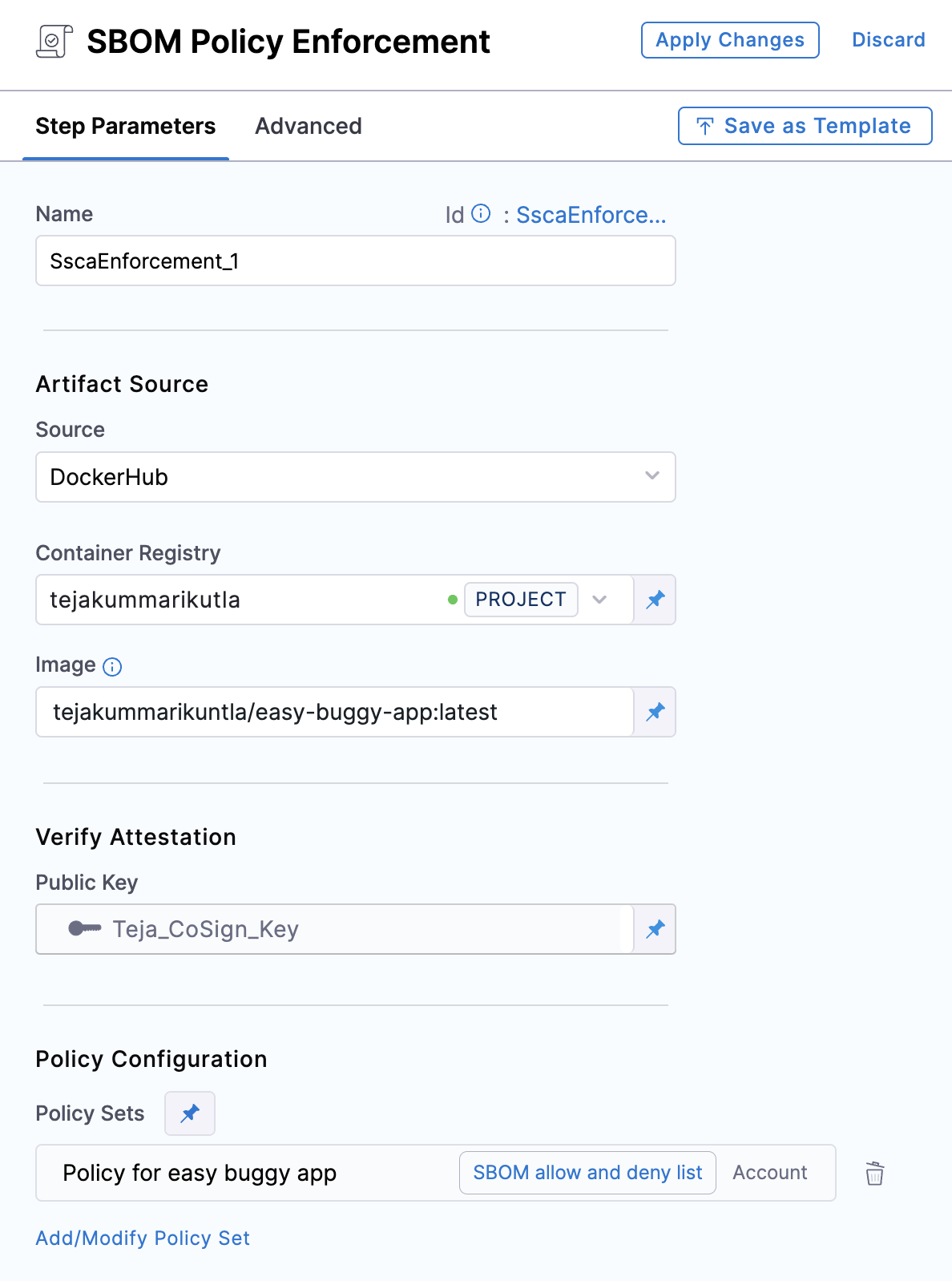
The SBOM Policy Enforcement step has the following settings:
- Name: Enter a name for the step.
- Source: Set the source, which can be DockerHub, ECR, GCR, ACR or Repository. Depending on your selection, a unique set of fields will appear, each specific to the source you've chosen. Address these fields as required, this is similar to configuring the source in SBOM Orchestration step. For more details of what each field entails, please refer to the documentation on SBOM Orchestration. If you are using DockerHub, you can follow along.
- Container Registry: Select the Docker Registry connector that is configured for the Docker-compliant container registry where your artifact is stored. Given that this step is to verify the attestation, read-level permissions should be adequate.
- Image: Enter the name of your image with tag, such as
my-docker-org/repo-name:tag. - Public Key: Select the Harness file secret containing the public key to use to verify the authenticity of the attestation.
- Policy Sets: Select the policy set that you want to use for enforcement. You can select multiple policy sets from Account, Org or Project.
Run the pipeline
When the pipeline runs, the SBOM Policy Enforcement step does the following:
- With the artifact details, the step verifies the authenticity of the attestation.
- Applies policies defined in the specified policy set.
- If violations are detected based on the policy evaluation criteria, the pipeline may issue a warning and proceed, or it may generate an error and terminate.
- Records policy violations and shows them on the Supply Chain tab on the Execution details page.
SSCA evaluates the components described in the artifact's SBOM against your policy definitions. For a component to pass the evaluation, it must meet these conditions:
- The component must not be denied based on the rules in the
deny_list. - The component must be allowed based on the rules in the
allow_list. - If the
allow_listhas multiple sections, the component must be allowed by all sections. For example, if theallow_listhaslicensesandsupplierssections, then the component's license must be allowed according to thelicensessection, and the component's supplier must be allowed according to thesupplierssection. If the component fails to pass either section, the policy evaluation fails for that component.
All components must meet the conditions described in both the allow_list and deny_list to fully pass the policy evaluation.
You can review policy violations on the Execution details page in Harness. For more information, go to view pipeline execution results.